
Acceptance criteria Modbus
Modbus has long been a widely accepted industrial standard for communication between devices such as sensors, control systems, and other industrial components. It is reliable, simple, and, most importantly, it works. Two main variants exist: Modbus RTU, which uses serial communication, and Modbus TCP, which runs over IP networks.
Modbus TCP has become popular due to its compatibility with modern networks. However, despite its technical reliability, Modbus lacks fundamental security features as it does not support any form of authentication. This means any device or person on the same network could, in principle, send commands to the system, posing a serious risk.
Although encryption is technically possible, it is rarely implemented in practice. As a result, communications are often readable and modifiable by anyone with network access, including hackers or malware.
This risk is amplified by the fact that an increasing number of flexible energy-intensive devices, such as EV chargers, heat pumps, and home batteries, support Modbus TCP. In a coordinated attack (e.g. as in the FrostyGoop1 incident), malware could control multiple devices simultaneously, with potentially severe consequences for grid stability.
In theory, network segmentation (e.g. VLANs or dedicated subnets) could reduce this risk. In practice, however, such measures are rarely implemented in residential environments. Most households run everything on a single network, making it easy for malicious software to spread or abuse devices.
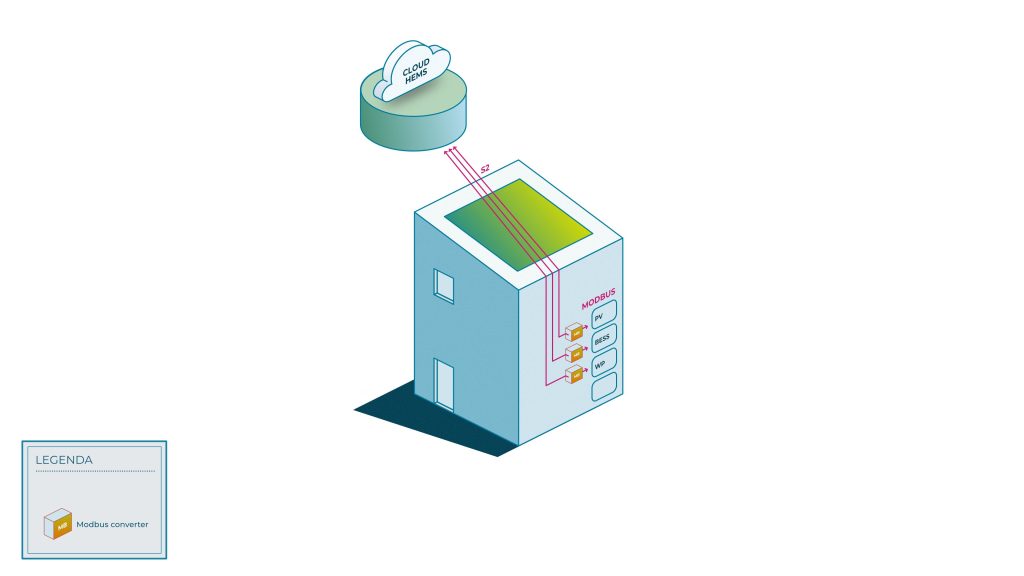
Modbus widely supported
Despite the obvious drawback with respect to security, Modbus is still widely supported by OEMs and manufacturers of flexible energy-intensive devices. It is therefore hard to ignore in any HEMS strategy. Therefore, ElaadNL is developing a solution to integrate Modbus into EMS/HEMS solutions in secure ways. The goal is to collaboratively develop a secure, practical, and future-proof Modbus integration within the broader HEMS ecosystem. We aim for middleware or proxy solutions that act as intermediaries between the HEMS and Modbus devices, that add layers of security (e.g. authentication or filtering). This also includes translation components that convert future-proof secure protocols (e.g. EEBUS or S2) into Modbus commands for those devices that rely on Modbus communication.







